If you have a package and you need to get it signed so that it runs without warning then you need to code sign the package or for that matter any application with a timestamp code signing certificate, this is shown in the digital certificate tab on the file as shown below:
When you examine this certificate you will notice is was signed back in 2015 for this application in question however with a timestamp certificate the expiry does not matter
Get the timestamp URL
Once you have chosen you code signing provider, for this example I will use Entrust you will get a URL link for code sign with, this link relevant to this example is shown below:
https://www.entrust.com/knowledgebase/ssl/time-stamp-url
When you look at the Entrust options you get a document signing URL or a code signing URL, and wer need the code signing URL which is this one (for this example)
Code Signing verification CANNOT be HTTPS, this particular requirement applies to CRLs as well
http://timestamp.entrust.net/rfc3161ts2
Right so now you have the URL, you cannot just download a PFX file as many providers, especially the secure ones no longer support software key providers and you need a software key provider to get a PFX that can be used in Windows.
Load up your token
You require hardware stored code signing certificate, this means you either need a security USB token (known as a security token) or a HSM which is a Hard Security Module which is usually a virtual appliance or a physical rack mount device.
Software storage of these code signing certificates, is my most reputable vendors, considered insecure, which means you will not be able to install this type of certificate to the software storage provider, which includes your computer and user certificate store built into Windows 🪟
Then you get the response from the authority, get the certificate installed on the hardware provider or key, with me so far?
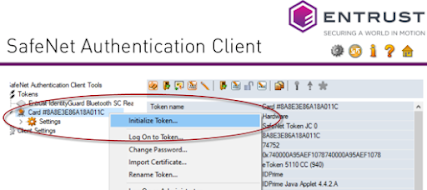
You will almost certainly need Safenet Authentication client which is a download you will need to get for your version of the OS, once you have this software and the token you will need to initialise the token, to do this plug it in the navigate to the settings (the cog under the entrust logo) then right click you token and choose Initialise token......
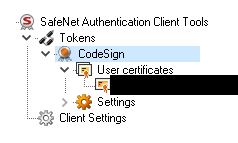
With the certificates details on the right side like this:
https://www.entrust.com/-/media/documentation/userguides/ecs_getting_started_code_signing_guide.pdf
Download signtool.exe for Signing
When you click install it will go off and do that action, once complete there will be no desktop icon or start menu icons as its a SDK, it except you to know where the files are, so if you navigate to this folder:
signtool.exe sign /tr http://timestamp.entrust.net/rfc3161ts2 /td sha256 /fd sha256 /a C:\path\to\program.exe