Firstly if you domain is federated this method will take precedence over the any methods you select here, the option your select in the user sign-in will only affect users if you moved from Federated to Managed - if you need to move from Federated to Managed you only need one command:
Set-MsolDomainAuthentication -Authentication Managed -DomainName <domain name>
To check these settings navigate to your ADConnect blade management in Azure by using this link:
https://portal.azure.com/#view/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/~/AzureADConnect
Once you are here you will notice that under the user sign-in option you will have a breakdown of your federated domains. the options below show we have Federation and SSO enabled and PTA Disabled for now.......

Change this options to Pass-though Authentication then you will need to click next, this will install the PTA agent on the AD-Connect server and then you should notice under the AAD blade in Azure, the pass-though authentication is now enabled, you will notice a orange triangle next to it, that is because we only have one PTA agent.......
Now ensure the standalone authentication server is running the Desktop Experience version of Windows, which is the one with the GUI, I only put this server as if you install Server Core (non GUI) the setup fails.
Run the setup for the agent called AADConnectAuthAgentSetup.msi to get this:
To turn that feature off, its Server Manager, then Local server then on the right it will say IE Enhanced Security Zone click the blue text and set this, ensure both are off.....

Then rerun your setup and the "error" should turn into this:

Login to this with your AAD admin account that is a global administrator, then once complete and authentication you should see a setup successful message:
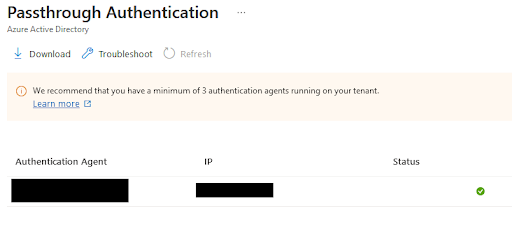
You will now notice under the AD-Connect blade in Azure and under user sign-in you will now notice you have 3 agents installed and the orange warning triangle has vanished, which is all good.
Then you see your 3 agents ifg you click on the pass-though authenticated listed with server names and the status of those agents, which for our example is 3 green ticks

We still have a federated domain, but one we make our domain managed, then all the users will sign-in via PTA and not ADFS, then after 5 days of that update, minimum, you can remove your ADFS infrastructure.