This assumes you have an existing "tenant" with 1Password, you will need to be an owner/administrator to complete this guide, let’s start with the login from this URL > https://start.1password.eu/signin?l=en
This will present you with your options, notice I am in the EU not the USA for the data location, you may not be depending on your requirements.
Login, power to the Bears
This example will be using "Dirty Bear Trousers" as below, so choose that a login as normal.
Configure Identity Provider
Once you have logged in you are looking for Policies as below:

Then you need to choose Configure Identity Provider as below:
Then you need to choose Azure and click next:

You will then require some details as you can see below, for we need to switch to the Azure portal, so hold that thought for now:
Configure Application Registration
You now need to visit the Azure portal over on https://azure.portal.com and sign in with an account with relevant access based on your security policies this will require Global Administrator.Once you are logged in you need Entra ID as below:

Then you need App Registrations

Then you need "New Registration"

Then you need to give it a name and choose Single Tenant as below:
You will then be taken to the overview like this:
Then click on the display name :

If should now look correct with the correct domain and you should loose the orange triangle of doom as below:
Now go back to the overview and get your application ID from that section, then you need to click on Endpoints, from this you will need the Application ID and OpenID Connect metadata document:
These details will need to be entered in this section of 1Password as below, then click Next:

Then you will get some details from 1Password like this:
Back to Azure you should still be in the application registration page, from the overview choose the Authentication then the Add a Platform option:
Then choose Single Page application as below:
Then add that URL here:
Then at the bottom of that window choose ID token and click configure....

Then you need to test the connection before you can commit this connection:
This will then ask for admin approval like this, you need to allow on behalf of organisation:
Then you get a confirmation that all is well, nice, but that is not all.....
Next is the "who to target below" so choose edit....
Then you want "Everyone" and within 5 days, if you have existing people make this longer for a switchover.....
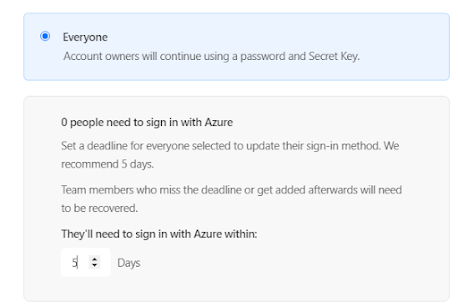
Then I have allowed Biometrics which requires Azure authentication after one day as below:
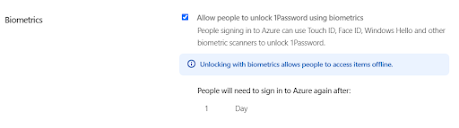
Then review the changes:
You need to read this as it people do not sign in within the deadline they will need their account recovered, for me this is fine, so hit the save button.
Add support for Mobile phones
Next is the "who to target below" so choose edit....
Then you want "Everyone" and within 5 days, if you have existing people make this longer for a switchover.....

Then I have allowed Biometrics which requires Azure authentication after one day as below:

Then review the changes:

You need to read this as it people do not sign in within the deadline they will need their account recovered, for me this is fine, so hit the save button.
Add support for Mobile phones
We not need Azure again and the same App Registration, back to Authentication however this time we need a Mobile or Desktop App:
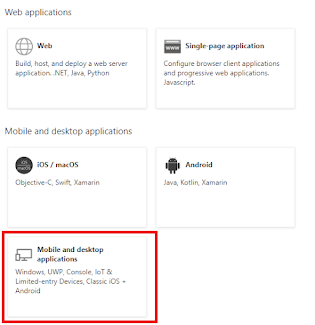
Which will point to the same document location as the previous Authentication for "single page" platforms, then configure that as well....

Which will point to the same document location as the previous Authentication for "single page" platforms, then configure that as well....
Activate Token Preferences
Then you Token Configuration as below:
Next, we need Enterprise Applications as below:

Find the application for us that is Dirty Bear Trousers the choose properties and change assignment required to "Yes" and ensure visible to users is "No"
Add the Users/Groups to allow access

Find the application for us that is Dirty Bear Trousers the choose properties and change assignment required to "Yes" and ensure visible to users is "No"
Add the Users/Groups to allow access
Then finally go to Users and Groups:
Then you need to add a group of people who will use this application, or for this example myself:
Owners v Team Members
If you are an Owner you will NOT see the identity provider login, instead you will see the normal 1Password login that looks like this:
However when you invite team members or guests which from the main menu choose people, use the invite button:
Then enter the correct e-mail for the user:
Now you are handed off to Azure to login using your security policies there, then you will be redirected back to 1Password.
Login Error for Team Members
If you get a login error like this then this means you have a MCAS or Entra Conditional Access policy enforcing MFA which interferes with the account creation process, this will also stop people using 1password - this is the error:
To fix this you have two options:

Then you need to add a group of people who will use this application, or for this example myself:
Owners v Team Members
If you are an Owner you will NOT see the identity provider login, instead you will see the normal 1Password login that looks like this:
However when you invite team members or guests which from the main menu choose people, use the invite button:
Then enter the correct e-mail for the user:
Now you are handed off to Azure to login using your security policies there, then you will be redirected back to 1Password.
Login Error for Team Members
If you get a login error like this then this means you have a MCAS or Entra Conditional Access policy enforcing MFA which interferes with the account creation process, this will also stop people using 1password - this is the error:
To fix this you have two options:
- Sign in from a location that requires MFA for signup and logins
- Exclude the 1Password application from the policy
Finding the policy that has joined sides with the rebel alliance
If you wish to exclude the 1Password application from MFA take a look at the user who was unable to login, so for that navigate to this path:
Microsoft Entra ID > Users then find the user
The click on sign-in logs and find the failed sign in logs
However you will notice these are all single factor but have not failed conditional access, the red box shows single authentication and the green box shows conditional access is all complete, so why the error?
Well you are not signing in Interactively this is non-interactive, so switch to non-interactive and you will then see the "Interrupted" event from Microsoft Graph with the failed conditional access
Then if you click on that event you will clearly see under the Conditional Access tab that the policy called "MFA - The one to rule all those Bears" is causing the issue:
If you again click on that policy you will see it requires MFA, which conflicts with the login process, so you need to exclude the application "Dirty Bear Trousers" from this policy.
Exclude in Conditional Access
Microsoft Entra ID > Users then find the user
The click on sign-in logs and find the failed sign in logs
However you will notice these are all single factor but have not failed conditional access, the red box shows single authentication and the green box shows conditional access is all complete, so why the error?
Well you are not signing in Interactively this is non-interactive, so switch to non-interactive and you will then see the "Interrupted" event from Microsoft Graph with the failed conditional access
Then if you click on that event you will clearly see under the Conditional Access tab that the policy called "MFA - The one to rule all those Bears" is causing the issue:
If you again click on that policy you will see it requires MFA, which conflicts with the login process, so you need to exclude the application "Dirty Bear Trousers" from this policy.
Exclude in Conditional Access
If you visit Entra Conditional Access











































